In April 2018, criminals hit Atlanta, GA with a ransomware attack that cost the city $2.6 million in recovery costs. March of this year saw Jackson County, GA paying a $400,000 ransom to bring their computer systems back online. And, Baltimore, MD has spent an astronomical $18 million to fix issues from a May ransomware attack.
These three examples comprise just a small number of the numerous cyberattacks that have targeted government organizations in the past few years. Cybercriminals are increasingly turning local- and state-level governments into victims of a particular type of cyberattack, called ransomware.
In a ransomware attack, a hacker infiltrates an organization’s computer system, blocking access to critical information or services. After successfully entering the network, the criminal begins to encrypt essential files or even block resources until the victim pays a ransom.
These ransoms are sometimes so significant that the organization continues to feel the impact months, or even years, after the hack. Although cyberattacks on government entities are nothing new, the magnitude and frequency of ransomware seem to have increased drastically over the past few years. There are a few causes we can attribute to this rise in crime:
Budget Constraints Are Hindering Cybersecurity Efforts
Often, government entities at the local level struggle to find room in the budget to implement proper cybersecurity practices. A 2016 International City/County Management Association (ICMA) survey revealed that 80 percent of local governments feel that a lack of funding is preventing them from achieving the highest possible level of cybersecurity.
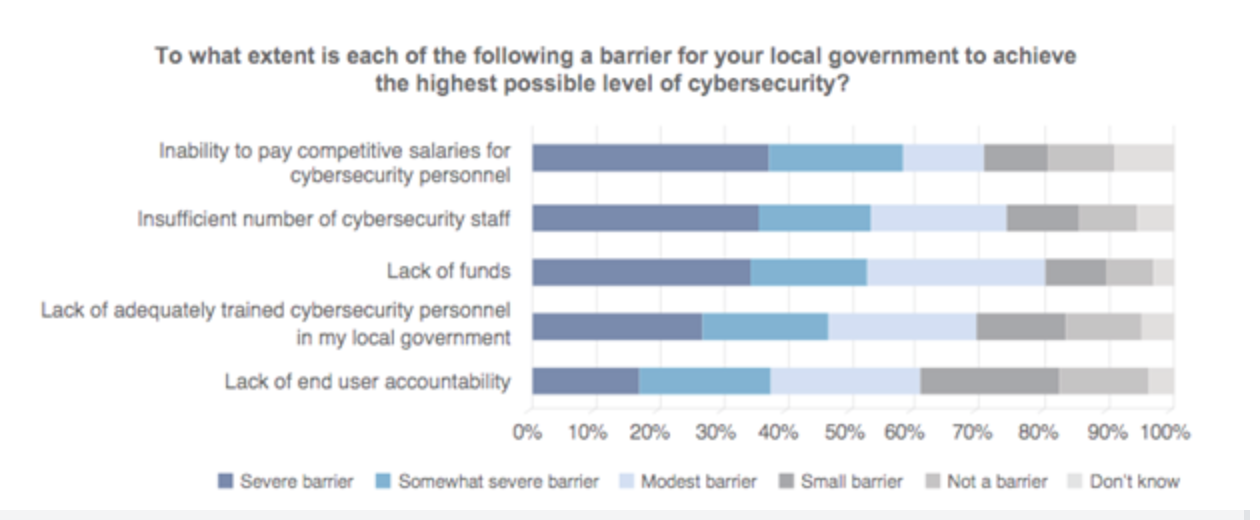 Over half of surveyed local governments cite a lack of funding as a somewhat severe or severe barrier to proper cybersecurity. | Source: ICMA Cybersecurity 2016 Survey
Over half of surveyed local governments cite a lack of funding as a somewhat severe or severe barrier to proper cybersecurity. | Source: ICMA Cybersecurity 2016 Survey
An additional effect of underfunding, local governments also report that they’re unable to hire a sufficient number of cybersecurity specialists due to an inability to pay competitive salaries.
On a positive note, government officials appear to be aware of the gaps in their networks’ security and support fixing them. Respondents in the ICMA survey stated that more support from department managers and top appointed officials would have the least effect on improving cybersecurity as they already support those efforts.
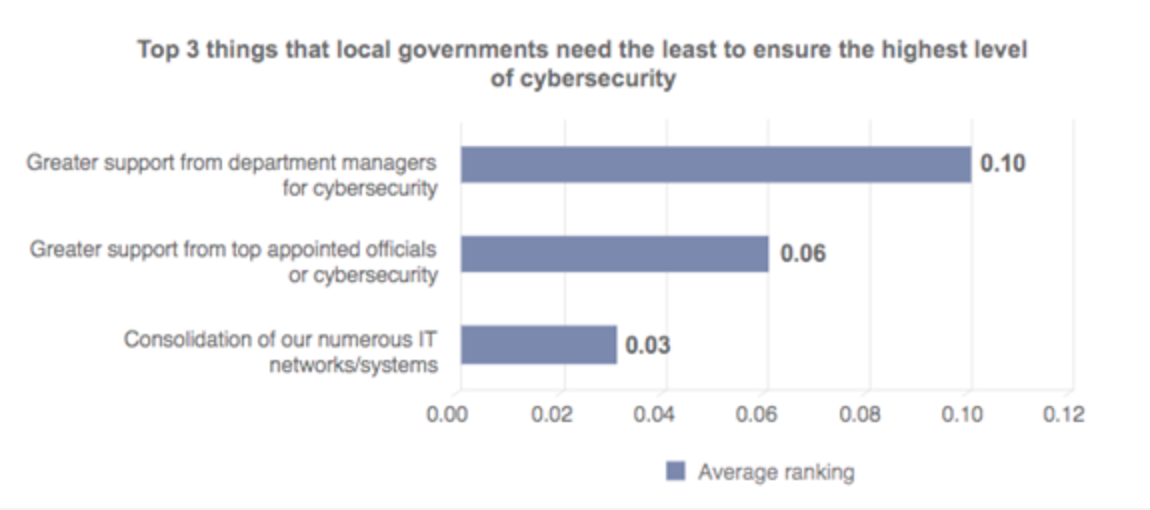 Department managers and top appointed officials aren’t the bottlenecks to better government cybersecurity. | Source: ICMA Cybersecurity 2016 Survey
Department managers and top appointed officials aren’t the bottlenecks to better government cybersecurity. | Source: ICMA Cybersecurity 2016 Survey
Poor Disaster Recovery Plans Amplify Ransomware Damage
Not only does insufficient funding cause lower barriers to potential attackers, but it also prevents organizations from implementing adequate disaster recovery plans. Many of the attacks on government organizations are as successful as they are because the victims fail to have a back-up strategy in place. A lack of contingency plans can quickly turn a thousand-dollar mistake into one that potentially costs millions.
The attack on Baltimore serves as a prime example of why organizations need to regularly back-up their data and create comprehensive recovery plans. The ransomware attack infiltrated several systems, including a parking fines database, government communications, and other payment platforms before officials were able to stop it. If the Baltimore government had backed-up these systems, operations most likely wouldn’t have been affected as they could then work from those back-ups.
Instead, the ransomware blocked use of those systems. And the government had to shut down the rest to prevent the attack from spreading. By the end of the attack, the city spent several months of working hours and millions of dollars to get the systems back online. If they had implemented a proper disaster recovery plan, those resources would have been saved.
Government Computer Systems Are Typically Out-of-Date
Inadequate cybersecurity funding isn’t the only issue, unfortunately. Government organizations at all levels fail to regularly update their software and hardware, sometimes using resources that are more than 50 years old. Antiquated computer resources often contain vulnerabilities that vendors will no longer (nor have an obligation to) patch, giving criminals effortless access to internal systems.
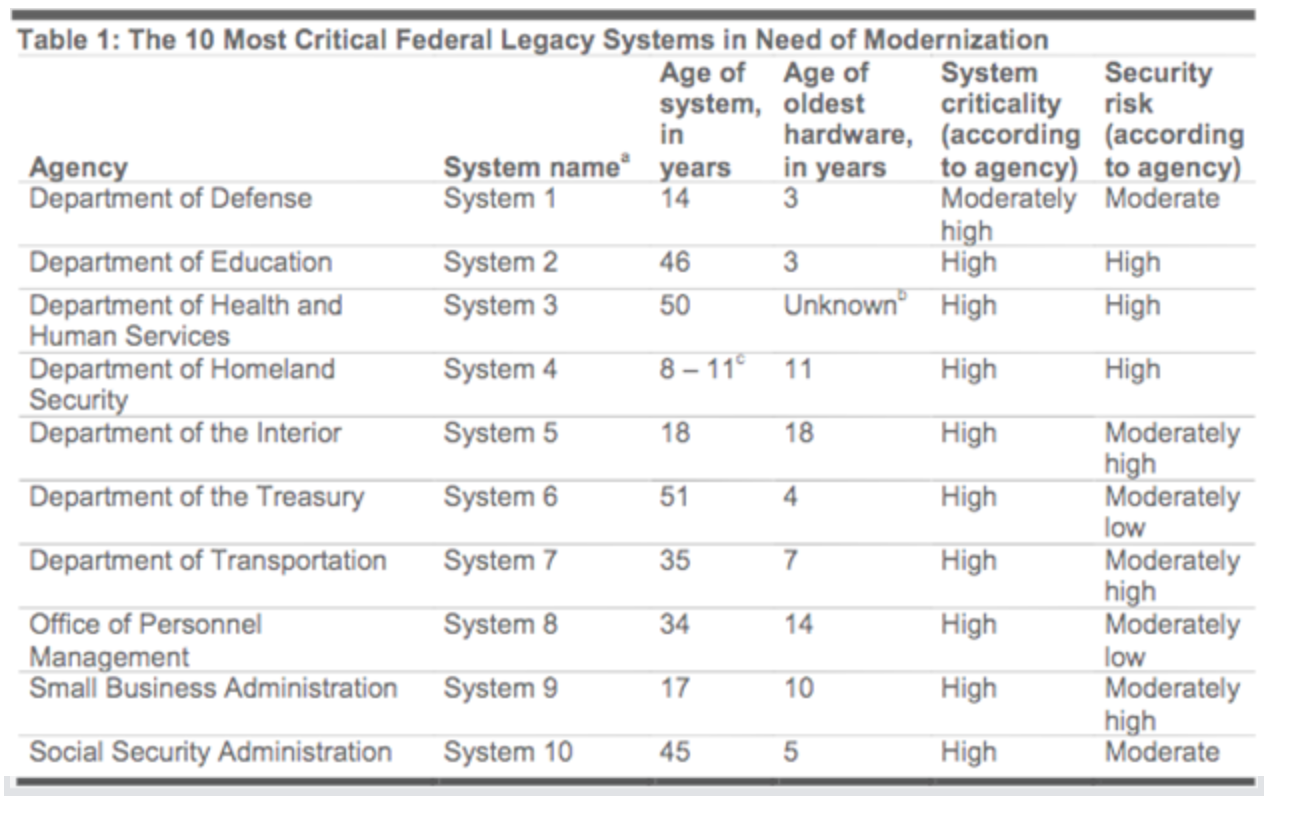 Even at the national level, the U.S. government is using severely out-of-date technology. | Source: United States Government Accountability Office
Even at the national level, the U.S. government is using severely out-of-date technology. | Source: United States Government Accountability Office
Several types of malware capitalize on these out-dated systems. Many utilize the EternalBlue vulnerability, for instance. EternalBlue is a bug found in old Windows systems that allows attackers to execute code on a victim’s computer. And although Windows has released fixes for the vulnerability, computer systems that haven’t been updated remain at risk.
Considering that some government computers are still running Windows 3.1 (1992), it’s likely that there are numerous systems exposed to the EternalBlue threat even today.
Continuing with our Baltimore example, many people believe that the ransomware behind the attack on the city, RobbinHood, took advantage of the EternalBlue vulnerability. If the organization had updated their software regularly, it’s likely that the ransomware would not have been a threat. Or, it would have at least been contained.
Government Organizations Are Relying More on Digital Systems
Unrelated to cybersecurity practices, criminals are more often targeting government entities simply because they’ve become more reliant on their digital networks. We’re seeing an apparent disconnect between the amount of funds governments are allocating to critical IT networks and the budgets of cybersecurity programs meant to protect them. Experts predict that local and state governments will spend almost $108 billion on information technology in 2019, up from the $103 billion spent in 2018. And, this trend will continue to proceed as the world moves further into the digital era.
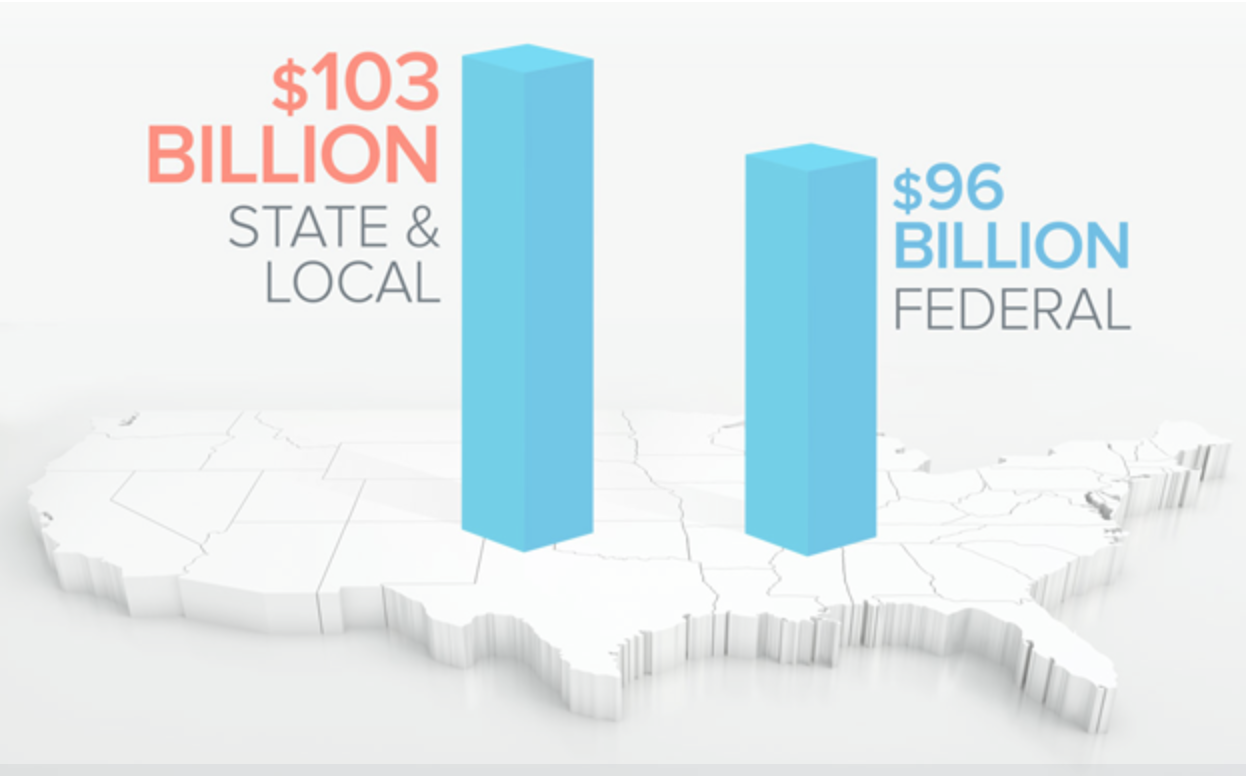 2019 IT spending is projected to grow nearly five percent from last year’s local and state spending. | Source: Govtech Navigator
2019 IT spending is projected to grow nearly five percent from last year’s local and state spending. | Source: Govtech Navigator
The actual ransom component of ransomware attacks is usually negligible in comparison to the cost of offline systems. The hackers in the Atlanta attack, for example, only demanded a $50,000 payment. So why was the final bill in the millions?
The criminals caused disruptions in five government departments, which prevented residents from paying bills, interrupted the court system, and halted vital communications, among other things. In other words, hackers blocked government officials from accessing the computer networks on which they had become reliant.
Doing so forced the Atlanta government to spend millions on emergency contracts to bring their infrastructure back online.
How Can Governments Protect Their Computer Networks?
The combination of limited budgets, a lack of cybersecurity staff, poor contingency planning, and years of technical debt present a bleak picture for the state of government cybersecurity. As a government organization, there are a few low-cost precautions you can take to protect your network. Most importantly, you need to regularly back up your data and create contingency plans for common threat scenarios. You may not be able to stop every hacker from attacking your system, but you can be well prepared if, or when, they do.
No matter the budget, it’s vital to become aware of the specific vulnerabilities your organization faces. Start by receiving a free cyber checkup today to discover where the security gaps in your organization reside.

