What Is Penetration Testing?
Penetration testing, or pen testing for short, is an authorized attack against your computer system to discover and simulate exploits of potential security vulnerabilities. Often, professionals describe it as ethical hacking. Penetration tests enable you to identify weaknesses in your business’s network that you may not have discovered on your own.
There is no single type of penetration test. Instead, the umbrella term includes a variety of distinct cybersecurity tests with a shared mission – finding vulnerabilities in your organization and demonstrating the impact of exploiting them.
In this penetration testing guide, we cover:
Penetration Testing Steps
Internal, external, web app – all pen tests follow a standard process. The usual penetration testing steps are as follows:
A pen tester’s first move is to gather information and perform reconnaissance. To do so, (s)he utilizes open-source intelligence (OSINT) tools to unearth any public information about your business, including (but not limited to):
-
Sensitive files
-
Exposed email addresses
-
Public code repositories
-
DNS registration
-
Data source breaches
OSINT reconnaissance is a passive technique that doesn’t involve probing any part of your organization or its network. The tester simply figures out what anyone else can through public information.
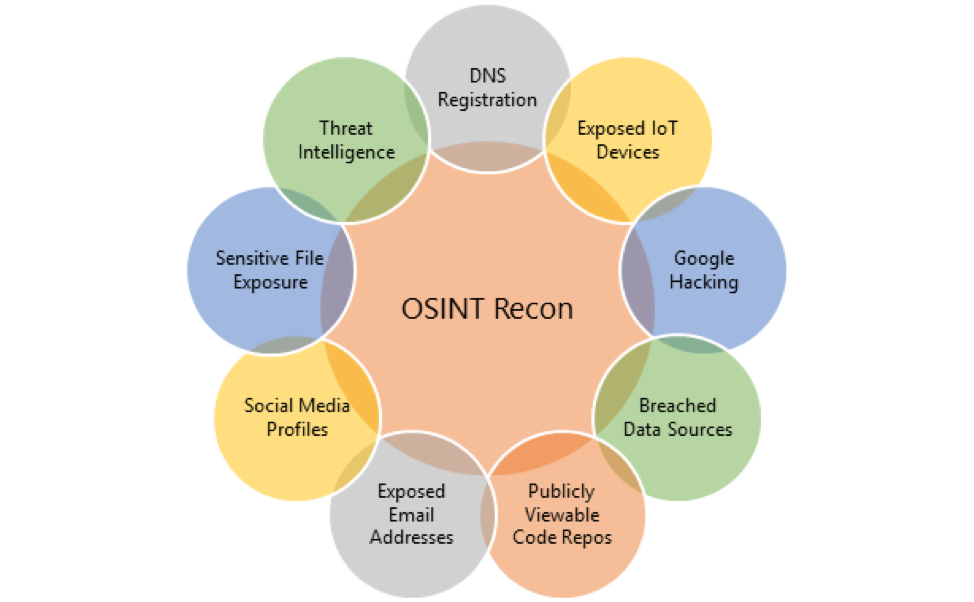 You’d be surprised at how much information a cybercriminal can discover about your organization through open-source intelligence.
You’d be surprised at how much information a cybercriminal can discover about your organization through open-source intelligence.
Depending on the type of penetration test, the tester will utilize several different tools to map out your networks, organization, website, and APIs in a more active manner. The overarching goal during reconnaissance is to learn as much as possible about your organization as well as its systems and networks.
Following reconnaissance, the tester launches scanning tools to discover potential vulnerabilities and attack vectors in your systems. The tester then thoroughly reviews the vulnerabilities s(he) found to weed out any false positives.
Now that the tester has a list of your organization’s security weaknesses, (s)he attempts to gain access to your system, sensitive data, and privileged functions. Once inside, (s)he works to elevate privileges, pivot through the network/application, and analyze the potential damage of a successful attack.
This execution step is the bread-and-butter of penetration testing. Whereas vulnerability scans stop once they reveal weaknesses, penetration tests continue on to examine what effect those weaknesses could have on your business if left unpatched. An experienced pen tester can chain together “low” and “informational” vulnerability scan findings to expose vulnerabilities that are “critical” in actuality.
Remember, the pen tester is only simulating an attack, so your system won’t experience any damage throughout testing.
 Although pen tests vary in size and scope, they generally follow the same process.
Although pen tests vary in size and scope, they generally follow the same process.
Most importantly, pen testers document their actions throughout all the penetration testing steps and compile a report upon completion. The report includes:
-
discovered threats,
-
the risk of those threats,
-
any sensitive data the tester could access,
-
how long the tester was in the system undiscovered,
-
and steps to remediate any vulnerabilities.
Black Box vs. White Box Penetration Testing
One way that penetration tests vary is through the amount of information a tester receives. The level of organization information you hand over dictates whether you run a black box or white box test.
In a black box penetration test, the tester receives no information about your network infrastructure. (S)he effectively simulates an attack that an outside cybercriminal would perform. Although black box tests are the most effective as they emulate a real-world scenario, they’re your most expensive option.
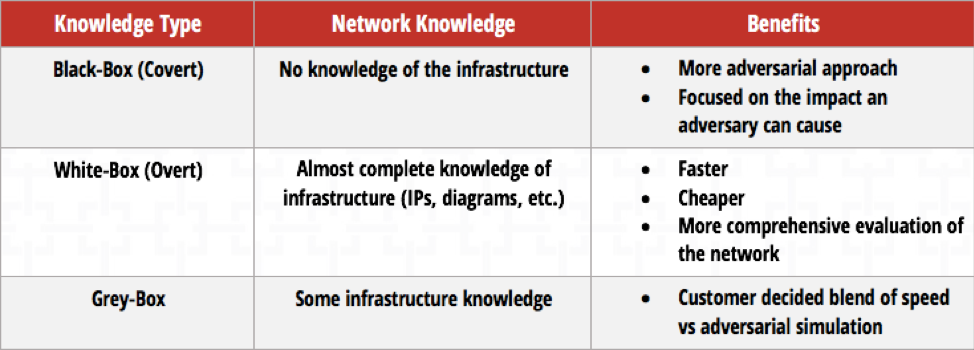 Testing with different levels of information has distinct advantages and disadvantages.
Testing with different levels of information has distinct advantages and disadvantages.
In a white box pen test, the pen tester has comprehensive information about your computer network. This type of testing is typically faster and cheaper than black box testing and may uncover vulnerabilities that a black box penetration test wouldn’t. However, it does a poor job of simulating real-world scenarios.
Finally, you’ve got grey box testing. As you could probably guess, grey box testing mixes aspects of white and black box penetration testing. In a grey box test, you give the tester some information about your infrastructure but still withhold certain details.
Types of Penetration Testing
Penetration tests come in all shapes and sizes. Some focus on specific aspects of your business, such as your data storage procedures, while others take a more holistic look. The following are four of the most common types of pen tests, plus one additional test that you should have in your cybersecurity arsenal as well.
 Penetration tests examine all aspects of your business, both internal and external.
Penetration tests examine all aspects of your business, both internal and external.
External Network Penetration Testing
External network penetration testing simulates an attack by an external threat on your business. The tester doesn’t have access to any administrative roles or login credentials and usually attacks via the Internet.
This type of test identifies firewalls, routers, and other perimeter devices as well as the services you allow through them. With that information, the tester creates attacks on those devices through HTTP/HTTPS, SMTP, POP, and other common protocols.
Benefits of External Network Penetration Tests
The primary benefit of external network testing is discovering how an outside hacker could damage your company. It helps you stay one step ahead of your adversaries or any cybercriminals.
External network tests also reveal the confidential information (e.g., login credentials, private keys, and SSH data) you’re inadvertently sharing to the public.
Internal Network Penetration Testing
Opposite of an external test, an internal network penetration test simulates an attack stemming from inside your organization. It assumes that an attacker is an employee with access to your network or a malicious user who’s gained access.
The reconnaissance stage of an internal network penetration test includes passive and active techniques. During passive internal reconnaissance, a tester collects network traffic to later identify network ports, hosts, protocols, and services. Active reconnaissance involves sending network traffic to discover additional network properties like users, operating systems, and domains.
Once again, the tester uses the information (s)he reveals in the reconnaissance step to expose and validate any vulnerabilities. Regarding internal network penetration testing specifically, the tester is looking for:
-
Weak credentials,
-
Encryption flaws,
-
Insecure session management,
-
Authentication flaws,
-
And other weaknesses
Benefits of Internal Network Penetration Tests
Internal network tests are vital to determine the extent of damage that an in-house attack can cause. In this way, it allows you to mitigate the risk of insider threats proactively.
Additionally, internal pen tests help you identify gaps in your internal security mechanisms and formulate solutions to those gaps.
Web Application Penetration Testing
Web application penetration testing, not surprisingly, focuses on specific web app and API vulnerabilities. In this type of analysis, testers check that you’re implementing appropriate information security controls to preserve the confidentiality, integrity, and availability of your application.
A web application pen tester begins by crawling and fingerprinting your application. During this process, (s)he identifies user roles, application entry points, web services, APIs, related apps, and third-party hosted content. The tester also probes API endpoints to reveal syntax and functionality.
Following the standard procedure, the tester then works to expose web application and API specific vulnerabilities. (S)he implements proxy servers, web app scanners, fuzzers, and manually-directed traffic to find the top OWASP application flaws, such as:
-
Injection,
-
Broken authentication (at an application level),
-
Sensitive data exposure,
-
Cross-site scripting,
-
Broken object-level authorization,
-
A lack of resources and rate-limiting,
-
Among several additional categories.
Additionally, web app testing exposes any of the OWASP top ten API risks. These risks include (but aren’t limited to):
-
Broken authentication (at an API level),
-
Excessive data exposure,
-
Security misconfiguration,
-
And improper assets management.
Benefits of Web Application Penetration Testing
Most importantly, web application pen testing reveals flaws in web apps and APIs before a breach occurs in production. And like external pen testing, it also discovers any sensitive information you may be leaking to the public.
Overall, application-specific testing tends to uncover vulnerabilities that standard internal and external pen tests usually gloss over.
Cloud Pen Testing
Often, organizations misconfigure cloud services, leading to problems such as public data buckets. Cloud penetration tests search for vulnerabilities in your cloud configurations and reveal those issues.
They scan services like Azure, Google Cloud, and Amazon Web Services (AWS) for weak credentials and confidential information. And they also identify the appropriate rights and roles for users in those services. Doing so reveals any instances in which a user or system has access to a part of the network in which they shouldn’t.
When using cloud services, there’s a shared responsibility of security between your organization and your service provider. Whether you’re implementing SaaS, PaaS, or IaaS, there are still steps you need to take to secure your data, application, operating system, etc. Cloud pen testing reveals the areas of which you’re responsible and whether your security practices pass muster.
Benefits of Cloud Pen Testing
As with the previous types of penetration tests, cloud pen testing exposes vulnerabilities before attackers have a chance to take advantage of them. Cloud testing reveals whether you’re leaking any private user data, authentication credentials, or any other confidential information from your cloud services.
With companies like Capital One and Facebook receiving major blowbacks for recent cloud data breaches, you need to protect yourself.
Social Engineering Testing
Although not technically a pen test, social engineering testing is crucial to stellar cybersecurity. Even if your computer system is completely secure from a software and hardware perspective, you still need to account for human-error risk.
Before launching an attack on a computer system, many criminals will attempt to gather credentials through social engineering. Social engineering testing simulates those efforts through several means – such as sending phishing emails to your employees, for instance.
 Social engineering tests unveil weaknesses in the human aspect of your cybersecurity. | Source: Phishing.org
Social engineering tests unveil weaknesses in the human aspect of your cybersecurity. | Source: Phishing.org
Benefits of Social Engineering Testing
Human-error tends to be the most challenging cybersecurity threat to overcome. Implementing social engineering testing enables you to nip potential problems in the bud. It reveals which employees (or users) are most susceptible to social engineering, making it simple to target them for additional training and education.
What to Look for in a Pen Testing Company
Pen testing is a necessity for any reputable organization. There are only so many vulnerabilities you can discover internally. Bringing in an outside perspective guarantees that you test and account for as many threats as possible.
Finding a quality penetration testing company can be a daunting task, however. How do you separate the legitimate companies from the duds?
Well, you can start by examining the certifications of the penetration testing company that you’re considering. The cybersecurity industry contains a handful of industry-standard organizations that provide accreditation only to the individuals that pass their rigorous criteria.
Other than checking for certifications, you need to choose a penetration testing company that you trust. Ask for references and see if you can get a sample of one of their testing reports. Failure to supply either of those things is a visible red flag.

