Last year alone, blockchain and cryptocurrency users reported nearly $3 million missing from social engineering thefts, such as phishing. Because of the broad reach and often unreported nature of these crimes, the total amount is likely much higher, making social engineering one of the top blockchain security issues for enterprise companies.
What Is Social Engineering?
Social engineering is an attempt by a malicious party to obtain some of your private, personal information. In the blockchain industry, this information usually includes your private keys or login credentials. Some social engineering attempts even fool users into handing over their cryptocurrency directly.
There are several types of social engineering, and criminals are creating new strategies every day. Let’s examine two of the most popular tactics in the blockchain space.
Phishing
Due to the community-oriented nature of the blockchain industry, phishing is a popular social engineering choice for criminals. In a phishing attempt, a thief sends you an email or message pretending to be a company with which you usually interact. These messages use an almost identical branding to the actual company and may come from an address that’s similar as well.
They’ll ask you to send over your credentials so that they can fix an issue with your account or enter you into a giveaway. And more often than not, they put you under a short time crunch to further the pressure. Once they have your credentials, they clear out your account.
In February 2018, Bee Token, a decentralized Airbnb, had their initial coin offering (ICO) hijacked by phishers. The scammers got hold of Bee Token’s pre-sale email list and reached out from a phony email account to offer an early investor discount. They collected nearly a million dollars in one day from unsuspecting victims.
Other than losing the million dollars directly to scammers, the Bee Token team also lost a significant number of potential investors who decided not to invest after learning about the scam.
Copycat Websites and Social Media Accounts
Similar to phishing efforts, copycat websites and social media accounts trick victims into thinking they’re interacting with a trusted name.
To further the believability of the ruse, copycat websites may also buy ad space on Google. Although Google tries to prevent this type of manipulation, there are always sites that slip through the cracks. Once you enter your credentials on a phony website, your account is immediately compromised.
 Copycats aren’t limited to websites. Apps fall victim as well. Source: Twitter
Copycats aren’t limited to websites. Apps fall victim as well. Source: Twitter
Burglars mainly use phony social media accounts to conduct fake giveaways. Although not so much anymore, Twitter was once a hotbed for giveaway scams. A profile imitating Elon Musk, for instance, would comment on a post by the real Elon Musk to promote a giveaway.
The contest instructions are simple: Send 2-5 ETH to a particular address, and you receive 20-50 ETH in return. Except you never get your prize.

The copycat profile is always identical to the actual one. The profile picture, bio, and displayed name are the same. Even the handle could be something similar (i.e., @elonmuskk instead of @elonmusk).
How to Protect Your Customers From Social Engineering
As a blockchain business, you should have multiple stops in place to protect your customers from social engineering. Often, when a customer becomes a victim, they blame the company, so it’s imperative that you educate them on how to spot social engineering attempts.
MyEtherWallet (MEW), a popular Ethereum wallet service, is a prime example of excellent customer phishing and social engineering education.
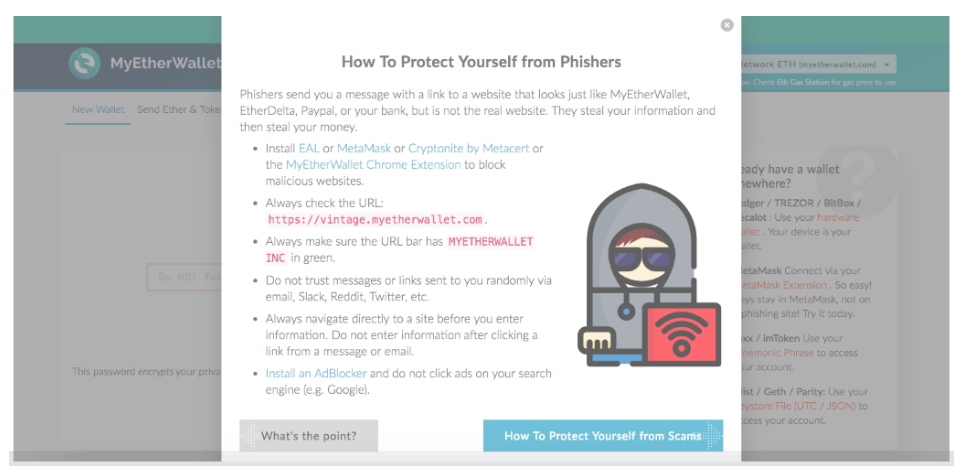 MEW makes sure their users know about phishing. Source: MyEtherWallet
MEW makes sure their users know about phishing. Source: MyEtherWallet
Immediately after landing on the webpage, MEW guides you through a pop-up of valuable information. One of the pop-up slides is wholly dedicated to phishing and how to avoid it. While this level of prevention may be overkill for your business, it demonstrates the importance of educating your customers.
At the minimum, you should have your official communication channels prominently displayed on your website, including social media accounts. Doing so enables users to quickly and easily check the validity of any message they receive. And it should go without saying, but you need to secure your customers’ personal information using industry best standards.
Additionally, it’s wise to require multiple forms of identity verification for users to log in or perform critical tasks. These checks can include two-factor authentication (2FA), email confirmation, SMS codes, security questions, or even biometrics in some instances.
How to Protect Employees From Social Engineering
While social engineering attacks on users remain isolated to the victims, an internal attack affects everyone. When an employee falls victim to social engineering, it has the potential to harm every single customer, or even the business itself.
It may seem obvious, but you need to train employees on how to spot phishing attempts and other types of social engineering. Beyond that, it may be worthwhile to test your employees with white hat phishing and social engineering efforts. It’s better for you to discover the weak links in the chain before an outside threat does.
Like precautions for customers, you should have multiple forms of identity verification for critical business functions. For additional security on those actions, require authentication from multiple employees so that one corrupt account can only do minimal damage.
Quick Tips For Customers and Employees
DON’T Click on suspicious links.
DO Type URL addresses directly into the address bar.
DON’T Tell anyone your login credentials or private keys.
DO Enable multiple forms of verification (like 2FA).
DON’T Feel pressured to send over any information with which you’re uncomfortable.
DO Verify any giveaways or critical support emails with multiple sources.
Adapting to Phishers and Social Engineers
It’s unlikely that phishers and other social engineers will ever stop their efforts. The cost is relatively low for attackers, and the payoff, if successful, is substantial. Because of the potential return, criminals are always trying out new social engineering tactics.
We only scratched the surface of social engineering in this article. Other than phishing and copycats, you’ve got vishing, quid pro quo, pretexting, and baiting, among a handful of different techniques.
Although implementing the precautions from above should thwart a sizable number of social engineering attempts, you need to tweak and adapt your security strategies with each new type of endeavor. And that involves staying proactive and aware of the latest attack strategies.
To learn more about phishing, social engineering, and other blockchain security issues, download our 2018 Blockchain Security Threat Report.

