As the Internet and the rest of the technological world become more open, cybercriminals are increasingly utilizing OSINT to gain intel on their victims. Since 2013, the number of Google searches for “OSINT” has risen over 500 percent, and that trend isn’t slowing down anytime soon.
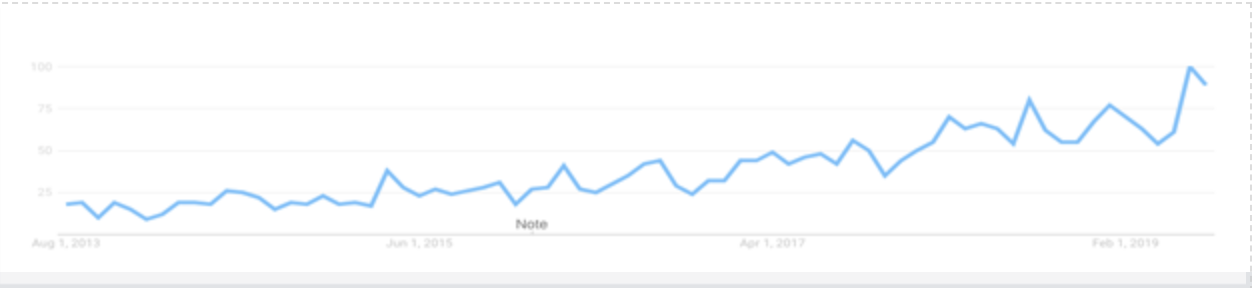 Google searches for ‘OSINT’ continue to climb in the open technology landscape. | Source: Google Trends
Google searches for ‘OSINT’ continue to climb in the open technology landscape. | Source: Google Trends
Before diving into the specifics of criminal OSINT activity, though, let’s take a step back and go over the basics.
What Is OSINT?
OSINT, which stands for Open Source Intelligence, is publicly available data that reveals information about your organization. This information ranges from relatively harmless data, like social media accounts, to critical vulnerabilities, such as public S3 buckets and login credentials.
Not all OSINT data collection is malicious. As a business, you can utilize it to discover vulnerabilities in your company. Individuals also commonly capitalize on OSINT for activities like phone number lookups and viewing historical site snapshots.
Hackers, though, utilize OSINT to perform reconnaissance on their targets. A quick Google search for “OSINT tools” exemplifies the sheer number of resources that criminals have at their disposal. OSINT Framework even provides a categorized list of hundreds of OSINT tools that anyone can use.
 This image shows a minuscule representation of the publicly available list of OSINT tools. | Source: OSINT Framework
This image shows a minuscule representation of the publicly available list of OSINT tools. | Source: OSINT Framework
What Information Can Hackers Gather With OSINT?
There’s a seemingly endless amount of information that hackers can gather about your business using various OSINT techniques. The following are the most critical.
Phishing Targets
It’s not efficient for criminals to target every member of your organization with a phishing attempt. Using OSINT, though, they’re able to discover, and eventually target, the employees that have administrative access to critical business applications. Here we outline a simple example.
Hackers utilize LinkedIn’s search function to quickly find employees with job titles like “System Administrator” or “Server Admin.” From there, they hop over to an email search engine such as Hunter to look for the appropriate email addresses. Even if they’re unable to discover the distinct addresses of specific employees, the attackers can get close. Many email search engines provide the typical naming convention for each company.
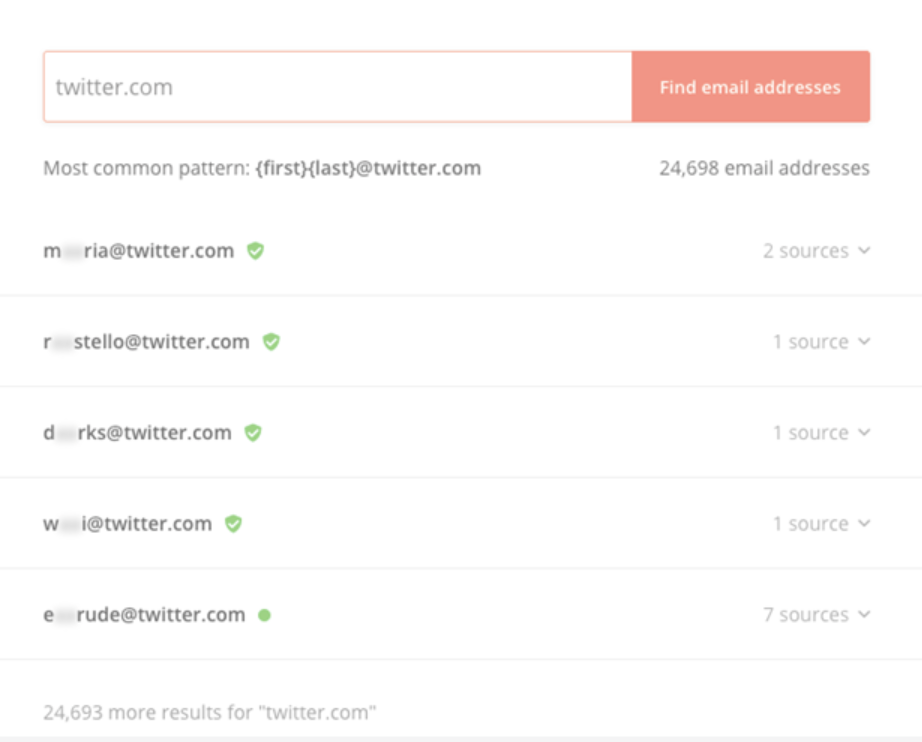 Email search engines make phishing research a breeze. | Source: Hunter
Email search engines make phishing research a breeze. | Source: Hunter
The phisher now has the business email addresses of critical employees. On its own, that isn’t a severe vulnerability. However, the attacker typically has other information as well. Through further OSINT revealing social media accounts, geolocations, usernames, and public records, our hacker can craft a shockingly accurate phishing email, tricking even the most vigilant of employees.
Credential Leaks
Humans are notoriously awful at password security. According to a 2018 report by LastPass, only 45 percent of businesses utilize two-factor authentication, and 50 percent of people don’t create different passwords for personal and work accounts. Once again, let’s walk through how a hacker could take advantage of these statistics using OSINT.
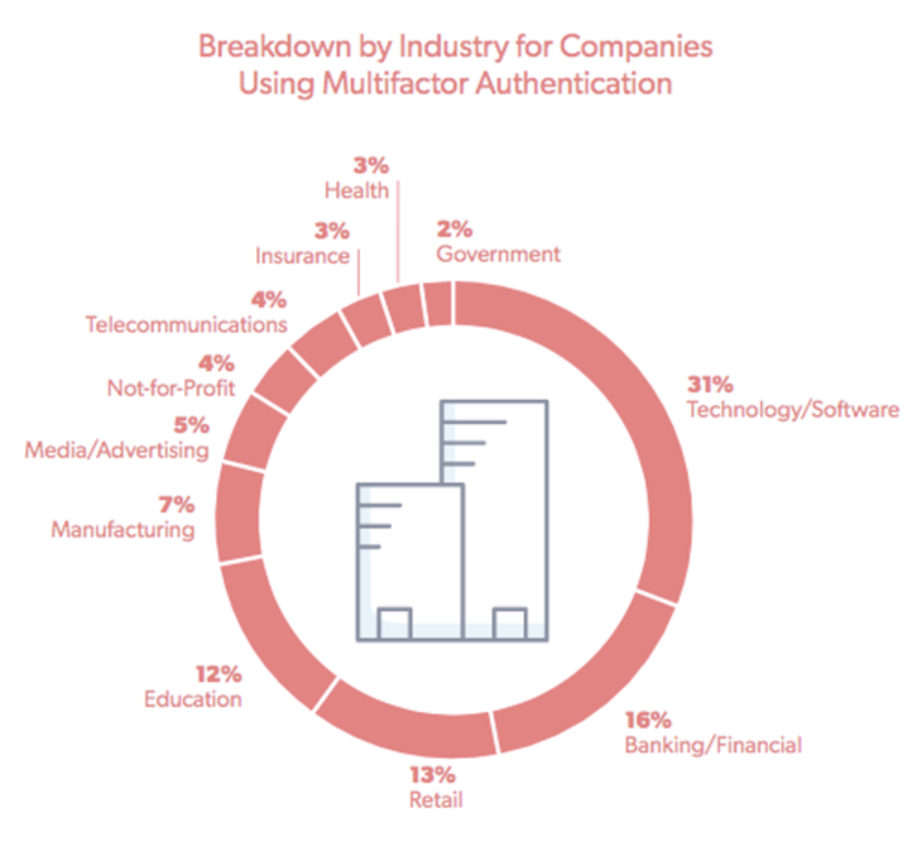 Technology/software companies are the most likely to implement two-factor authentication with banking/financial businesses placing at a distant second. | Source: LastPass 2018 Global Password Security Report
Technology/software companies are the most likely to implement two-factor authentication with banking/financial businesses placing at a distant second. | Source: LastPass 2018 Global Password Security Report
Brute-force guessing is a fine, although time-consuming, strategy to retrieve credentials. However, OSINT devices, like a downloadable list of exposed passwords, cut this time significantly. But, that list includes more than passwords. It also contains the number of times that a particular password has appeared in a data breach, effectively presenting you with a list of the most common passwords.
Once again, through social media searches, an attacker can discover which people hold critical roles at your business – positions with access to git repositories, for instance.
If only half of all people separate work from personal passwords, it’s safe to assume that even less separate usernames. So to an attacker, figuring out git repository usernames is a relatively trivial matter. Additionally, services like Namechk reveal whether a username is taken across numerous platforms, which enables attackers to validate their guesses.
With a list of verified usernames and common passwords, hackers can perform an ultra-efficient brute-force attack.
Exposed Servers, Devices, and Applications
OSINT expands beyond human vulnerabilities. There are also a plethora of tools that reveal network information about your business. Let’s take a look at another type of threat – DNS hacking.
A standard DNS hack begins with an attacker locating the nameservers for a target domain. A simple search through DNS Checker unveils this information.
From there, a hacker can attempt a zone transfer (data transfer between name servers). If the server is misconfigured, it will allow the transfer and send crucial details about your business’s infrastructure, such as its subdomains, to the attacker. With this information, a hacker can exploit vulnerabilities like unmaintained infrastructure or a server that’s missing critical security patches.
Tools, like SpiderFoot, help hackers connect the dots between geolocations, IP addresses, domain ownership, registrar servers, subnets, and other parts of a business’s infrastructure.
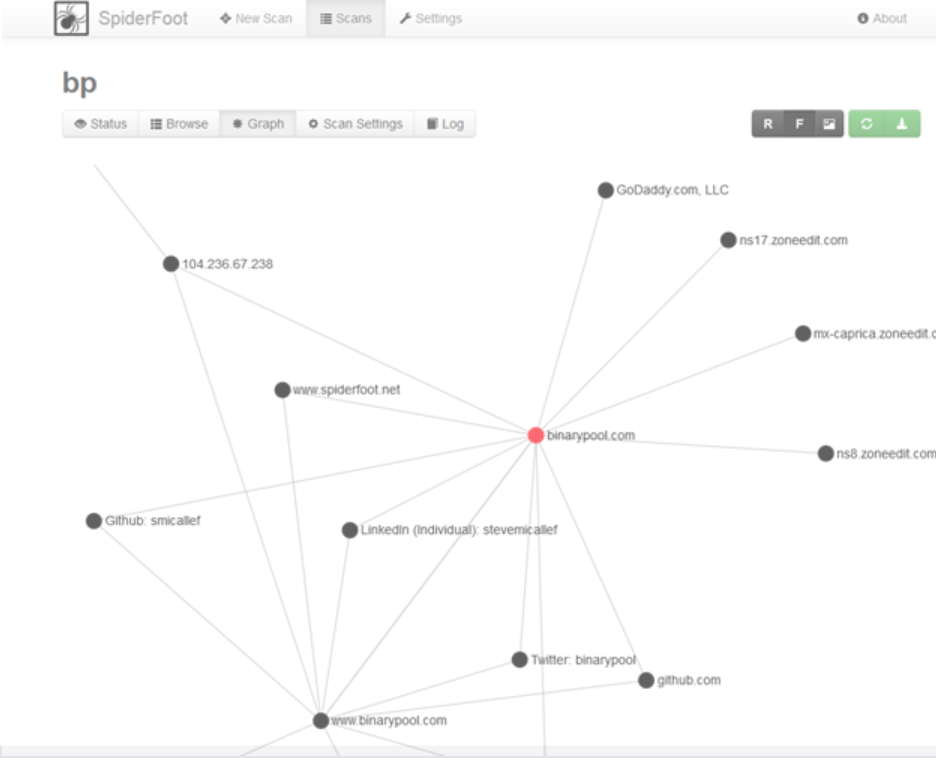 SpiderFoot presents the connections between OSINT data in a visual manner. | Source: SpiderFoot
SpiderFoot presents the connections between OSINT data in a visual manner. | Source: SpiderFoot
But as we mentioned before, hackers aren’t the only entities utilizing OSINT. Working with his own product, Steve Micallef, the creator of SpiderFoot, was able to gather some identifiable information about the annoying Elon Musk scammers currently plaguing the crypto industry.
Public S3 Buckets
Practicing proper Amazon Web Services (AWS) storage procedures is easy enough on paper, yet even the largest companies fail to do so. Hackers commonly exploit public S3 buckets to obtain user data, credentials, and a host of other confidential information.
With the growth of OSINT, we’ve also seen a rise in software that places efficient S3 bucket mining just a few clicks away. The folks at Gray Hat Warfare created a search engine dedicated to combing through public S3 buckets and exposing vulnerabilities. If you haven’t already, it’s imperative to search for your own business and discover the information you’re inadvertently revealing.
You should also routinely check the settings of your S3 buckets to ensure their privacy, and monitor them for any suspicious activity.
How to Protect Your Business Using OSINT
Because many of these OSINT tools are publicly available, you’re on equal footing with potential hackers. Perform the same checks that your attackers would to see what information your business is exposing to the world.
Not sure where to start? Run your business through our free OSINT checkup to see what vulnerabilities you may have.

